Hardware can be evil! How Anti Tamper Protection works
- Elias Themeßl
- 12. Feb.
- 3 Min. Lesezeit
Anti-Tamper Protection
Caution is advised when dealing with products that perform safety-critical functions. These often employ so-called anti-tamper protection mechanisms. These are mechanisms that make it difficult to open the device or even render it unusable if it has been opened. There are many different approaches, and the techniques have rapidly evolved over the years.
A relatively simple measure is the use of special screws. These require the use of special screwdrivers or special bits. Of course, this is not an effective approach to prevent devices from being opened, as there are countless suppliers of such special bit sets available online for little money.
If you encounter a screw for which you do not have a suitable screwdriver bit, there is a simple trick. Take a long, thin, and round piece of plastic. Heat the end of the plastic until it begins to melt slightly but does not burn! Press the heated side of the plastic rod against the head of the screw. The plastic will conform to the shape of the screw head. After cooling, it should be possible to unscrew the screw with the self-made "screwdriver."
Another measure manufacturers use to make opening difficult is the use of screws that can only be tightened but not loosened again. This is made possible by the mechanical design of the screw. The head of the screw is milled off or simply twisted off with some force after tightening. In this case, drilling is the only option available.
Gluing the plastic parts of the case is also a very popular method used by manufacturers. Opening without leaving traces is almost impossible. However, the use of hot air or solvents that soften adhesives can help. Even though this is only a weak protective measure, the process of opening can take quite some time.
Sometimes, certain dyes are added to the adhesives that adhere to the case. These are intended to indicate, for warranty reasons, if a device has been opened.
The use of stickers or seals on the packaging is also a popular method to ensure warranty. They serve more to make changes visible than to protect against opening.
If you buy a new device for personal use, it should have a seal, make sure it is intact and in place. Otherwise a so called supply chain attack could have happened.
Supply chain attacks are attacks where devices are intercepted and modified by criminals during shipping. For example, for espionage or stalking purposes. A well-known example of this is hardware wallets for cryptocurrencies. Criminals open these devices, make changes to the hardware, often designing and installing their own circuits. The wallets are then repackaged as closely as possible to the original and resold or sold through other means.
To protect yourself from such attacks, only buy original goods and preferably directly from the original manufacturer. Also, look for the presence of seals that indicate opening.
In many cases, manufacturers use ultrasonic welding to seal plastic cases. In this case, there are usually no visible grooves or weld points. In this case, the case must be drilled or cut open. A rotary tool of your choice with a grinding attachment is the right tool for such tasks.
A stronger measure against opening devices is the use of anti-tamper meshes. There are countless variations of these. A well-known method is to have contact points on the circuit board that are connected by metal inserts in the case. If a part of the case is removed, the electrical connection of the contacts is also interrupted. In such a case, it is usually too late, and the device no longer works after opening. When using anti-tamper meshes, several such contact points are placed on the circuit board to make opening as difficult as possible.
If this is the case, it is advisable to have a second identical device that has already been opened. By comparing the two devices, it is easier to determine where the contact points are located on the target device. It is a very delicate and time-consuming task to open the case and bridge the contacts simultaneously, but it is possible. However, it requires a lot of patience, experience, and dexterity.
The use of simple switches or light sensors inside the device can also deactivate a device as soon as it is opened and thus comes into contact with light.
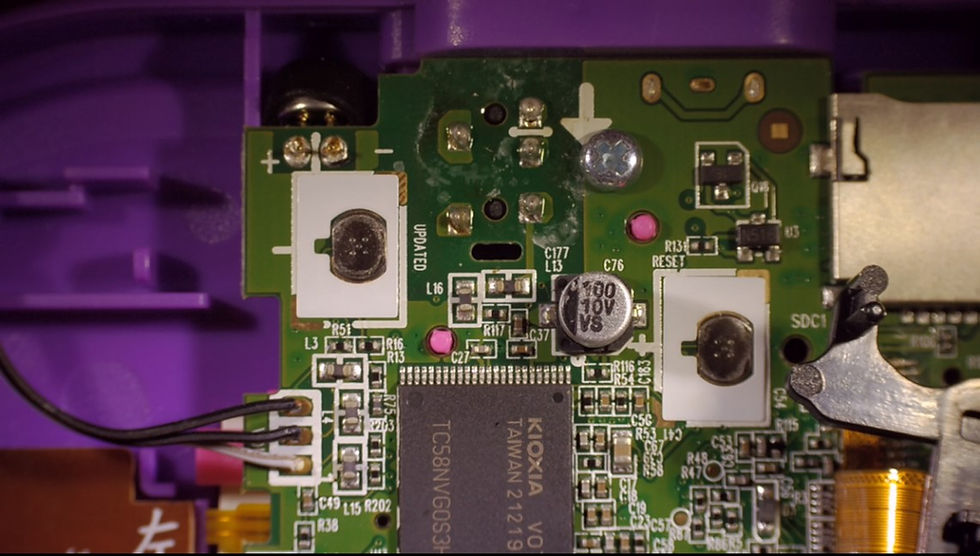
Above and to the side of the NAND flash memory, there are two switches on the circuit board that interrupt the contact as soon as the cover is removed. After opening the device, it no longer works.
Such techniques have been known for a long time but are still used. However, manufacturers are not idle and are constantly developing new methods to improve or refine the principle of anti-tamper meshes.
Commentaires